
Projects
CEIS 101 Course Project
Develop smart home automation and security system by designing the prototype in Tickercad, building the hardware with the components from the IoT. Tech Core Kit and programing within Arduino IDE. The smart home system will encompass various devices to monitor the condition of the home. This includes a door sensor to check whether a door is open or closed, a distance sensor to monitor for a possible home intruder, and automated light that turns on when it is dark.
![20211204_122752[1]_edited.jpg](https://static.wixstatic.com/media/07cc6f_8c069edb4b5c451eb10bba783d6e4acf~mv2.jpg/v1/fill/w_491,h_331,al_c,q_80,usm_0.66_1.00_0.01,enc_avif,quality_auto/20211204_122752%5B1%5D_edited.jpg)
Linux Project
I used the Linux operating system and created users, directories, and files. Managed the Linux resources including the Network adaptor. Created and executed shell scripts by using standard input, user-defind variable, redirection, file permissions and environment variables. Magaed user accounts by creating users and modifying groups.


Python coding project
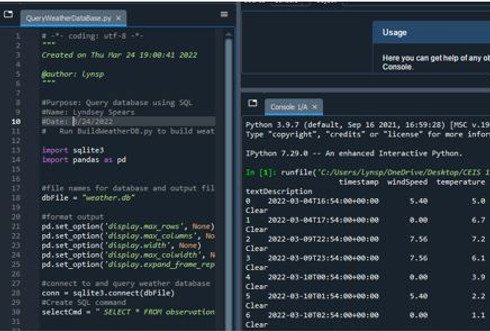
In this project I learned how to use Python to create a cloud based data which was gathered from US Government National ocean and Atmosphere Administration. A flow chart was created to show each step that would be taken within the project to show how the data would be retreived and analyised. The database created was to show temperature and humidity over a 2 week period.

Networking project
In this project I learned how to implement an IPv4 scheme to support a network by connecting to an SOHO router. Also show how to test the connectitivity amoung the two computers and SOHO router. The project was started with a class C network and divide its block of IP address into smaller blocks then confirgure the two Loopback interfaces on the SOHO router by using IP addresses of newly created subnets to simulate two LAN segments. Also a diagram was created to show a network diagram that depicts the interconnection of Computer 1 VM, Computer 2 VM and SOHO router VM.
Programming with objects
In this project I learned how to create programming using python to create classes for stocks. The first step was creating up a basic python code showing the averages for prices by setting up an environment. The next step was to create the classes needed to work with the stock and history data. Once the classes had an environment set up then a console-based interface was created for working with the stocks and the stock price history. Which was then processed by creating classes that were inherited from a base class. Then the following few step were to create an example chart to show stocks which then the code is used to create a chart from a file that was downloaded from Yahoo! Finance. With the full compile of the entire code a GUI was used to show the stock tracking that would be implemented by using the GUI code.
Introduction to Digital Devices
In this project I learned how to create a two traffic module with an emergency button. In this first part of the project we show the items that will be used to create our traffic light simulation. Then by using 2 bread boards a an ESP32 board set up the connections to create the simulation. As well as to push buttons were added to simulate an emergency stop and to simulate a cross walk button. For the final portion of the project and motion sensor was added to the project.
Fundamentals of Cloud Comp
Netw 211
In this project I learned how to use Microsoft Azure by working directly with virtual machines. During this project the first reviewed was viewing a virtualization and cloud infrastructure. Then the following items reviewed were cloud connectivity, cloud security by showing examples of virtual network security, compute data. Some other items reviewed cloud storage along with cloud monitoring and automation for clod usage.
Fundamentals of Information System Security
SEC285
In this project I learned about the threats and security issues that come with using secured and non-secured networks. During this project I learned the importance for setting up encryption keys with the use of cryptography and using a multifactor verification authenticator. Also include the risks managements that can come from attacks and defnese for networks. Along with creating a bring your own device policy, where a user or an employee may use there personal device on a companies' network for personal or company use.
Java GUI Application
CIS 355A
In this project, I learned how to create a prototype GUI application using Java and MySQL. This first step was setting up the UML class design and the overall structure that the customer/client would be presented with. While creating the simple I learned how to create and code the use of several items within Java such as radio buttons, JList, Tab menus, file menus, and several other items. The main concept for this project was to be able to set up a Java GUI application by creating a Landscaping that would allow a customer/client to choose whether they would want their yard covered in grass or gravel. As well as being able to save all customers using MySQL so the customer's information could be retrieved to provide any updates.
Data Structures and Algorithms
CEIS295
The project covered fundamental Data Structures ideas. The research includes an analysis of algorithm execution times. Possibility for practical education while working on the project. Another objective of using client classes and importing classes in Python is to help with object-oriented programming. Three distinct sorts of scenarios are shown in this project: a printer queue/service queue, a service center, and a contact center.
Fundamentals of Infrastructure Security
SEC290
This project serves as a foundational exploration into infrastructure security, where participants will gain practical experience in several critical areas. In the first module, exercises focus on vulnerability analysis using tools such as the Nmap Scripting Engine, alongside exploiting known Microsoft vulnerabilities like MS08-067 and MS17-010. The second module introduces intrusion analysis, using Wireshark to perform basic protocol analysis and examine common network attacks. In the third module, participants will dive into Open SSL, learning how to create and test SSL/TLS files for secure communication. The fourth module provides hands-on experience with Snort, an open-source intrusion prevention system, teaching users how to detect malicious network activity and configure Snort for real-time threat detection. The fifth module emphasizes live memory analysis, using Linux and Microsoft tools like Volatility, to analyze system processes and detect potential security breaches. Finally, the sixth module teaches how to configure iptables for network defense, covering scenarios such as time-based access, brute force prevention for SSH logins, and dynamic NAT. This comprehensive approach prepares learners for the fast-paced and ever-evolving field of cybersecurity.







